Configure SAML SSO with Okta, PingID and oneLogin
Federation is a collection of common standards and protocols to manage and map user identities between Identity Providers across organizations (and security domains) via trust relationships (usually established via digital signatures, encryption, and PKI).
NodeSource Orgs can now take advantage of Identity Providers (IdP) such as Okta, PingID and OneLogin by using NSolid’s new SAML integration to manage user access to NSolid and NodeSource Accounts.
SAML (Security Assertion Markup Language) is an open standard for exchanging authentication and authorization data between an identity provider and a service provider which can be used for SSO (Single Sign-on) for the NodeSource Account. The NodeSource Account is deployed ready for integration with the third-party SAML 2.0 compatible identity providers.
Requirements to set up SAML SSO
To set up Federated authentication via a SAML SSO Integration administrators are required to meet the following requirements:
- Enterprise Organization in your NodeSource Account
- Administration privileges in your NodeSource Account
- Administration privileges in your identity provider
Setup SAML with Okta
- Log in to your Okta Account as an administrator.
- Navigate to
Admin Dashboard > Applications > Add Application. - Click
Create New Appand chooseSAML 2.0as the Sign on method.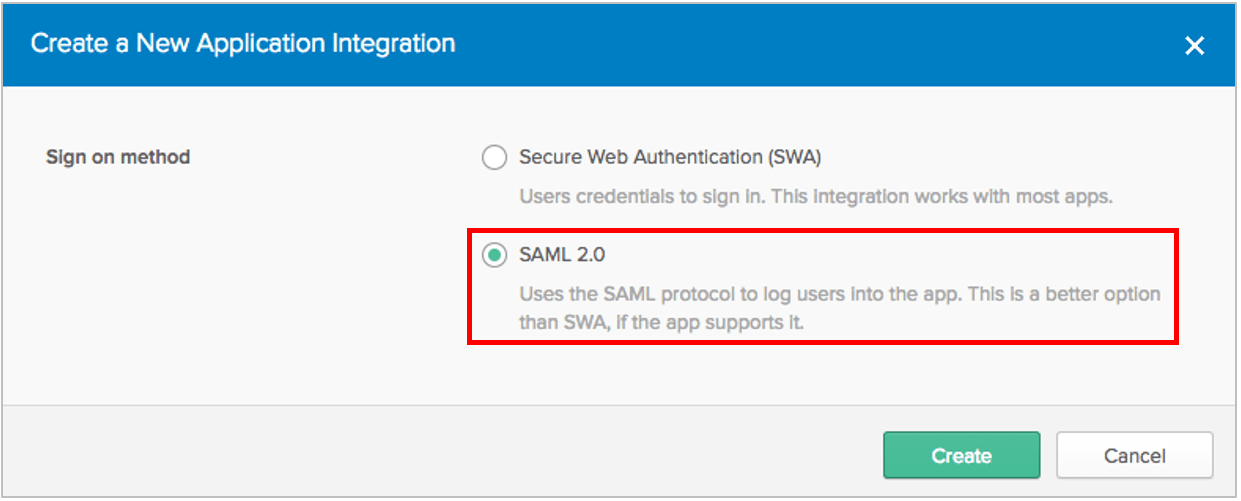
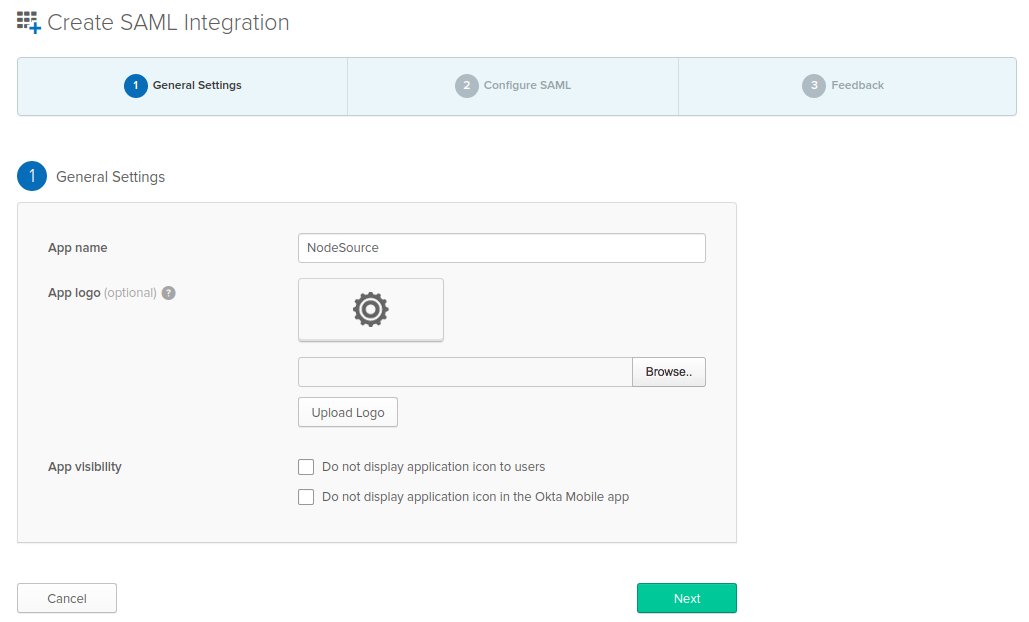
- Enter General Settings for the application, including App name and App logo (optional).
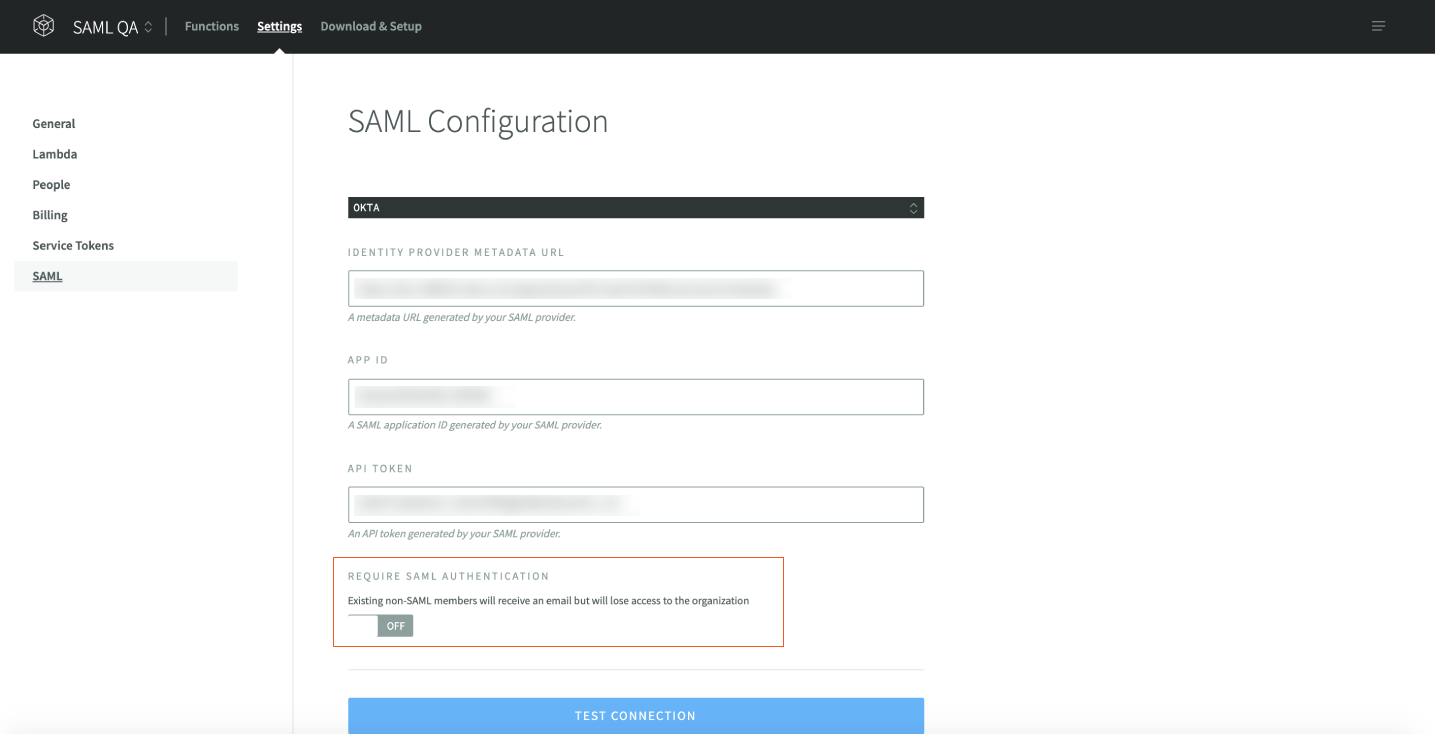
- Enter SAML Settings, including:
Single sign on URL: https://api.nodesource.com/accounts/auth/acsAudience URL: https://api.nodesource.com/accounts/auth/idp-metadataName ID format: unspecified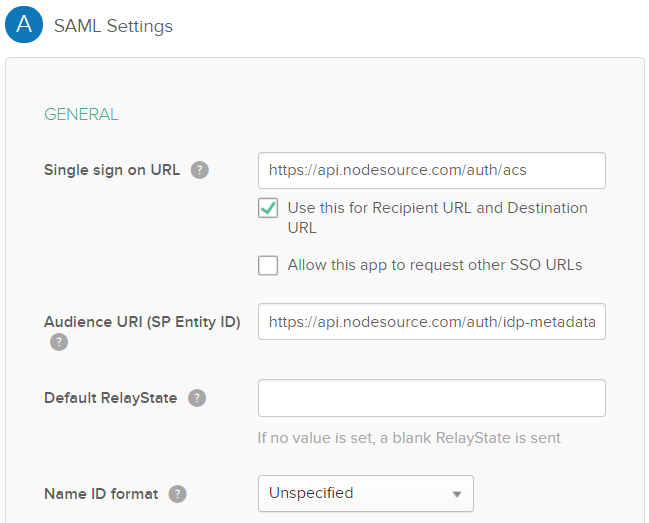
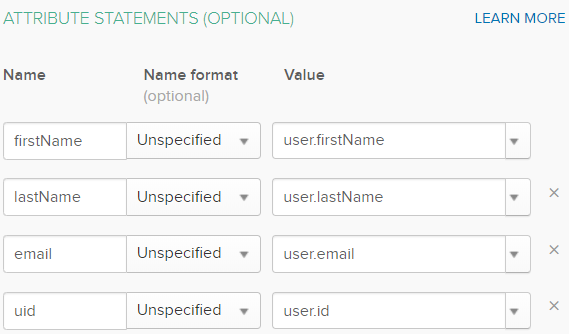
- Enter attribute statements as below, which will be used to map attributes between Okta and NodeSource.
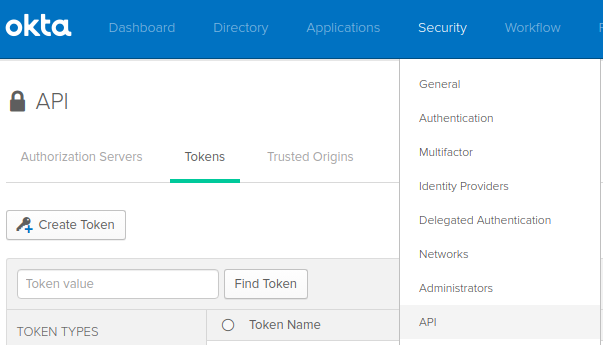
- Create a new API Token (Security > API > Tokens > Create Token)
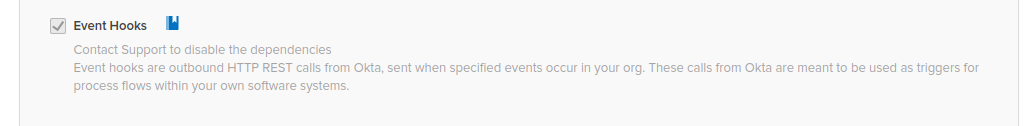
- In Settings > Features, enable Event Hooks to use SAML webhooks
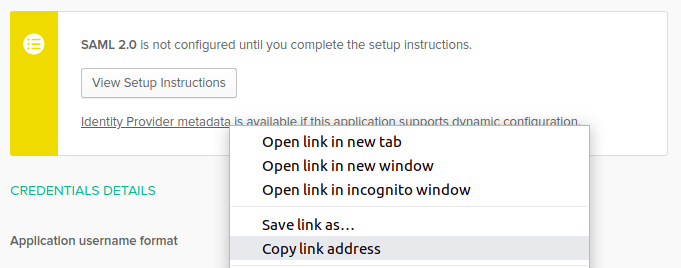
- In your SAML web app, Sign On > Settings, copy the link address of Identity Provider metadata:
- In your NodeSource accounts SAML settings, paste the values generated above.
Identity Provider Metadata URL: the link address of Identity Provider metadata in Sign On > SettingsAPP ID: in your okta SAML app page url, e.g., (https://dev-712690-admin.okta.com/admin/app/nodesourcedev712690_nodesource_1/instance/0oamwnctp4tW02lzL356/...), the string after instance/ is your APP IDAPI Token: a unique API token generated by your SAML provider.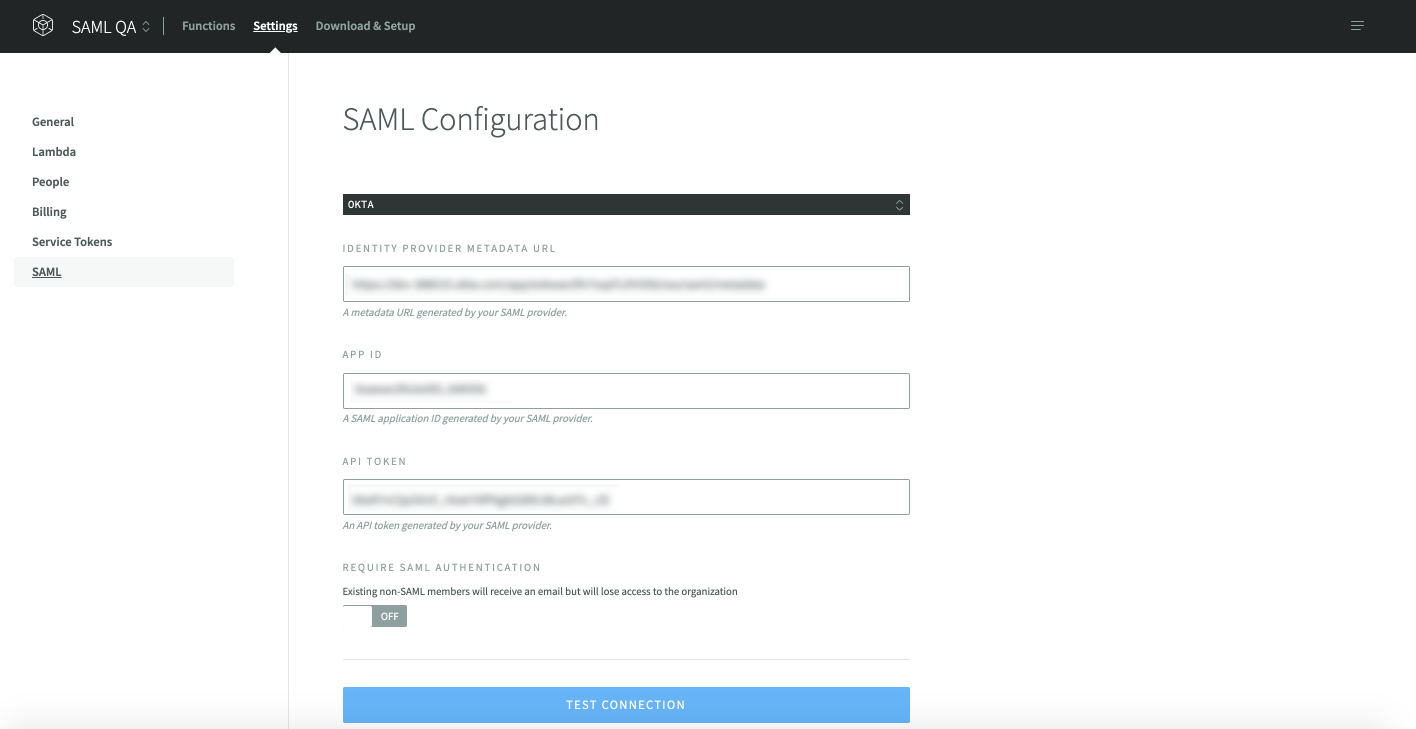
- Click
TEST CONNECTIONbutton to test the single sign-on connection.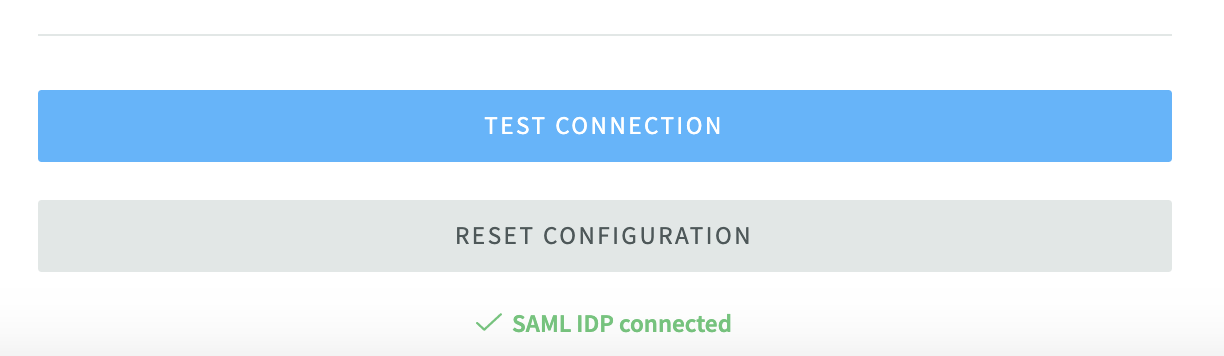
Use NSolid with Okta-based SAML
Users whose organizations chose to active the Okta integration, must sign into accounts.nodesource.com/signin first in order to accept NodeSource’s Terms and conditions. Once accepted users can directly access the console using their SAML SSO credentials.
See here for details.
Setup SAML with PingID(Ping Identity)
- Log in to your PingOne Account as an administrator.
- Navigate to
Applications. - In
My Applicationstab, clickAdd Applicationsbutton and chooseNew SAML Application. (IfNew SAML Applicationis disabled, you should connect to an identity repository first. See https://support.pingidentity.com/s/document-item?bundleId=pingone&topicId=fml1564020492091-2.html for more info). - Enter Application Details for the application, including
Application NameandApplication Description.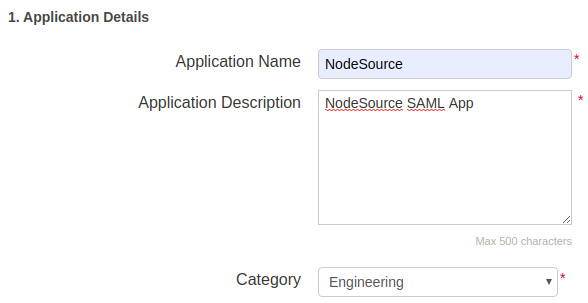
- Enter SAML Settings, including:
Assertion Consumer Service (ACS): https://api.nodesource.com/accounts/auth/acsEntity ID: https://api.nodesource.com/accounts/auth/idp-metadata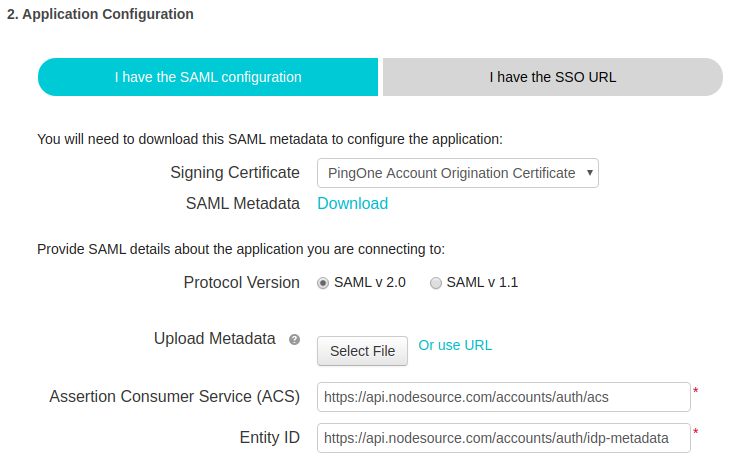
- Map the necessary application provider (AP) attributes to attributes as below. You can get your
orgIdfrom theSAMLtab on NodeSource Accounts.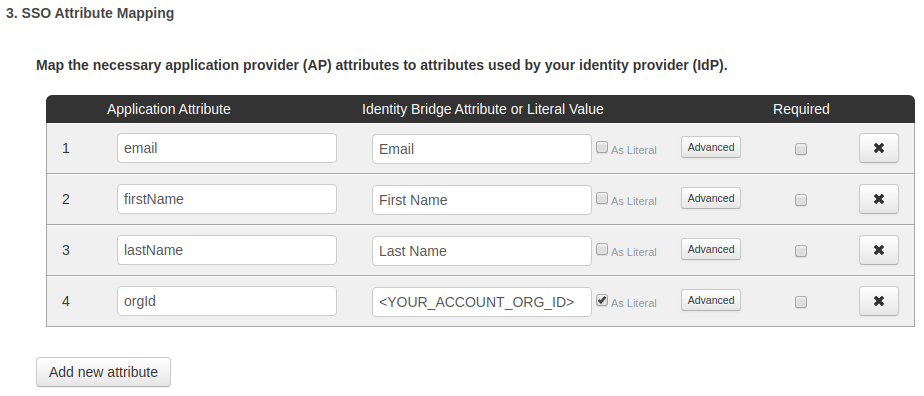
- Select all user groups that should have access to this application. Users that are members of the added groups will be able to SSO to this application and will see this application on their personal dock.
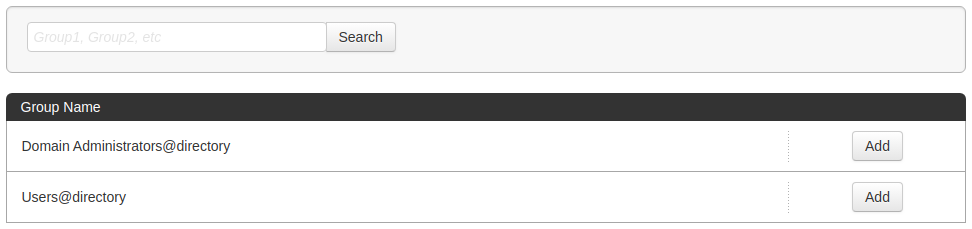
- Review Setup and click
Finishbutton. - Go to the
SAMLtab in your NodeSource Accounts, paste the values generated above.IDENTITY PROVIDER METADATA: Your identity provider metadata (XML)SSO URL: Single Sign-On (SSO) URL of your SAML App.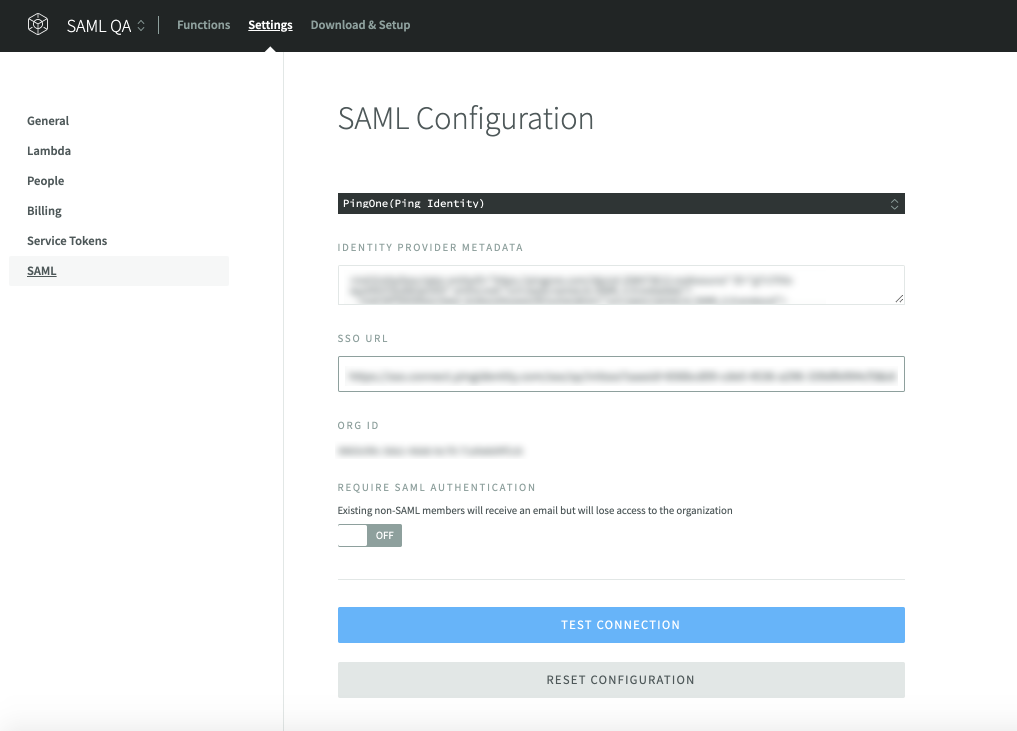
- Click
TEST CONNECTIONbutton to test the single sign-on connection.
Setup SAML with oneLogin
- Go to https://developers.onelogin.com/ and create an account.
- If you already have a oneLogin account, login as your organization's administrator and navigate to Apps > Company Apps > Click [Add App] button
- Enter SAML in the search box and select ‘SAML Test Connector (Advanced)’
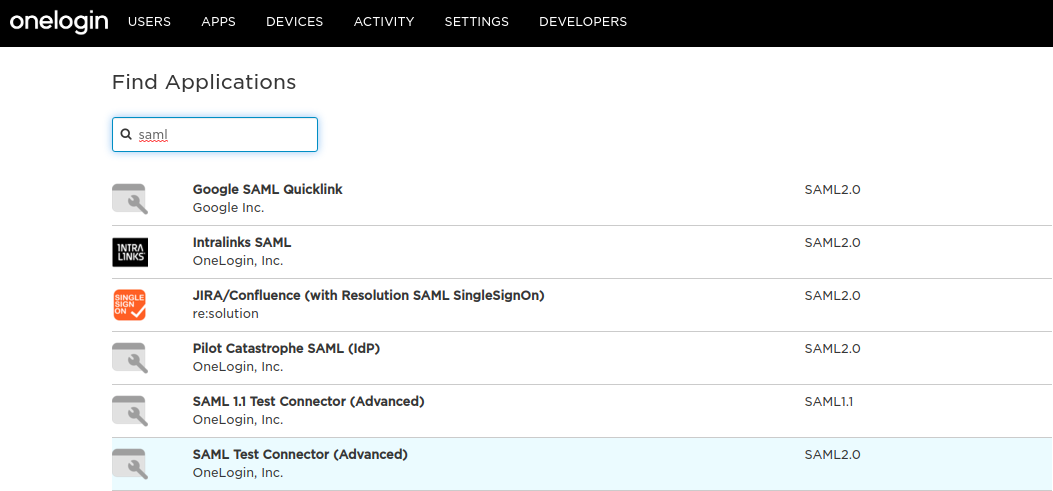
- Enter SAML in the search box and select the ‘SAML Test Connector (Advanced)’
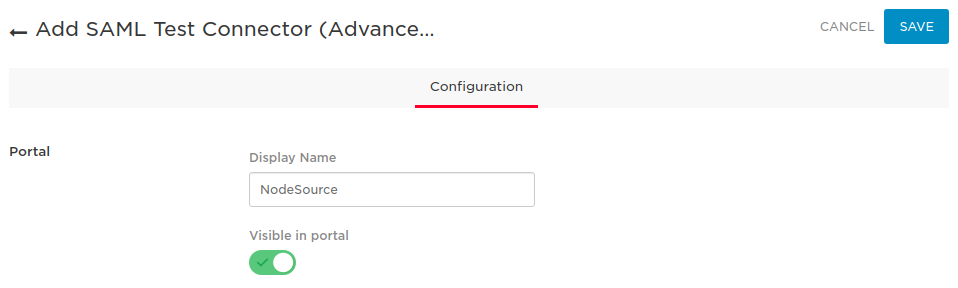
- Once selected apply the following configurations in the
Application Detailssection as below: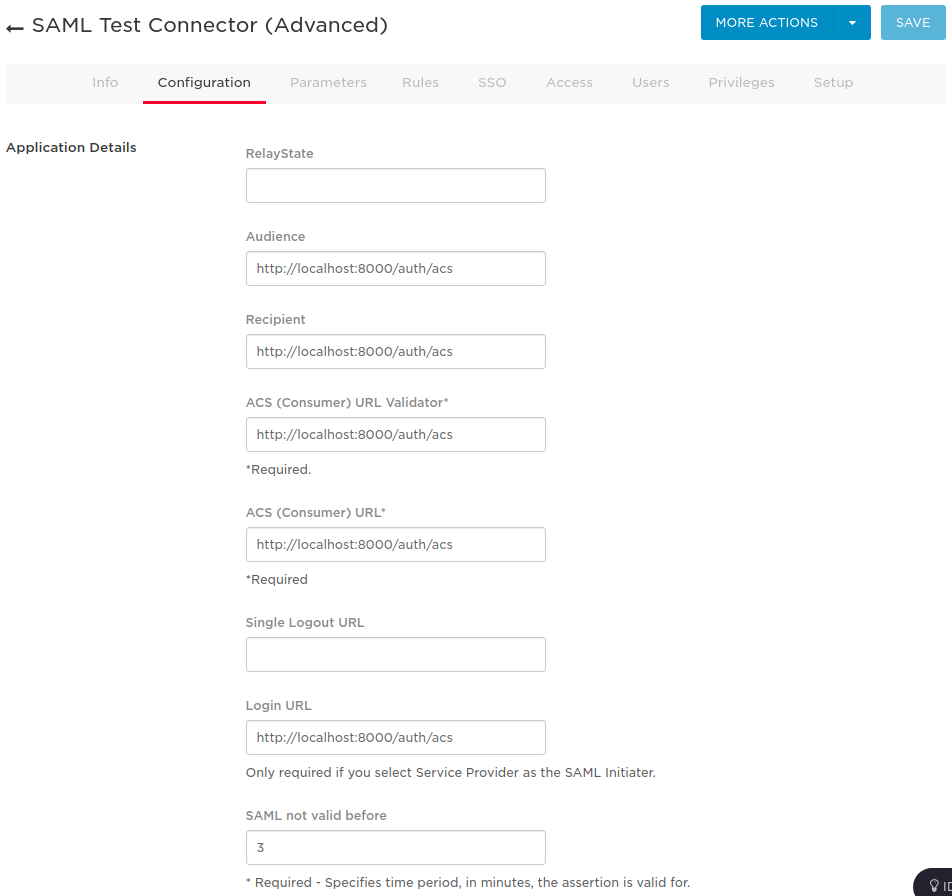
- Set
Parametersas follows: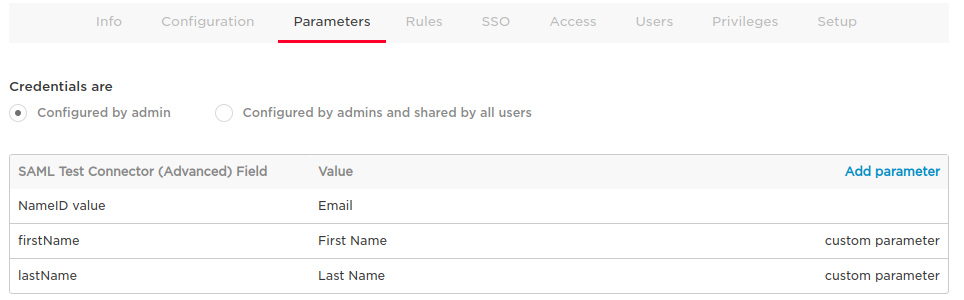
- Inside the SSO tab, click ‘View Details’ to get your X.509 Certificate:
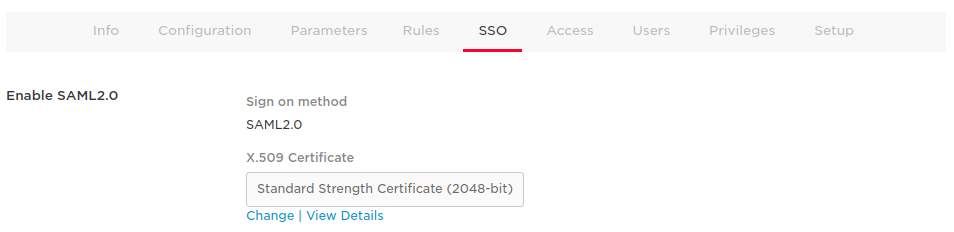
- To get your IdP metadata URL, click the ‘MORE ACTIONS’ button and right click on ‘SAML Metadata’ and copy the link address:
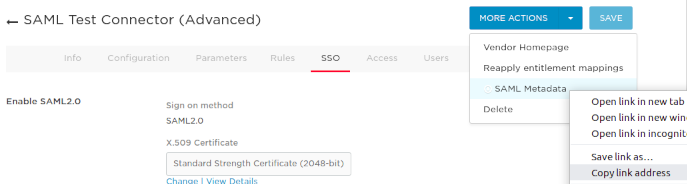
- Select
DEVELOPERS > API Credentialsto create your API Credentials as below:
- Click
New Credentialbutton and selectManage Alloption and save: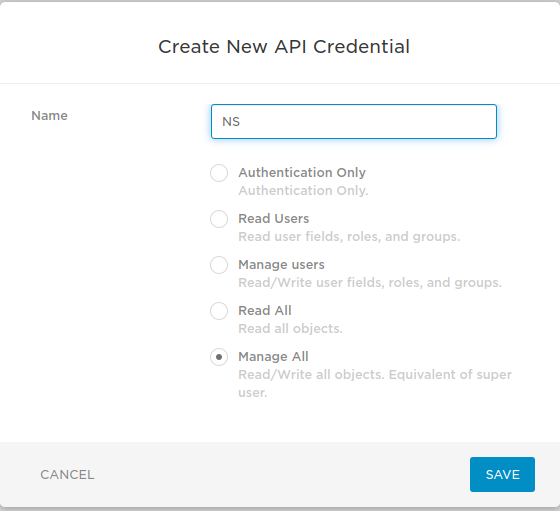
- Your API Credentials (
CLIENT SECRETandCLIENT ID) are created: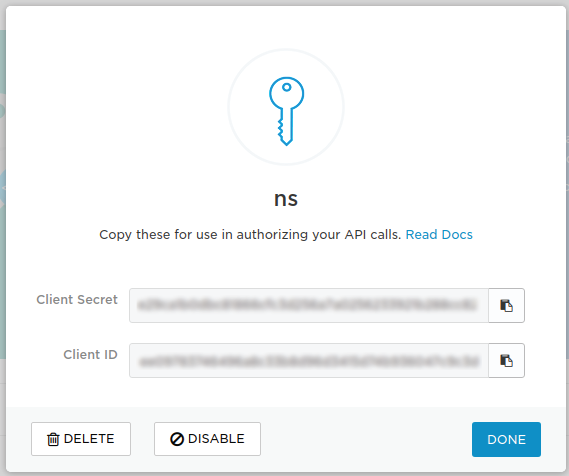
- In accounts,nodesource.com navigate to
settings > SAML. - Copy and paste the metadata url (step 9) in
IDENTITY PROVIDER METADATA URL. - APP ID: In your onelogin SAML app page url, i.e., (
https://nodesourcedev.onelogin.com/apps/646661/...), the number afterapps/is yourAPP ID - Also paste the
CLIENT SECRETandCLIENT IDyou generated in step 12 and input it in their corresponding fields as shown below: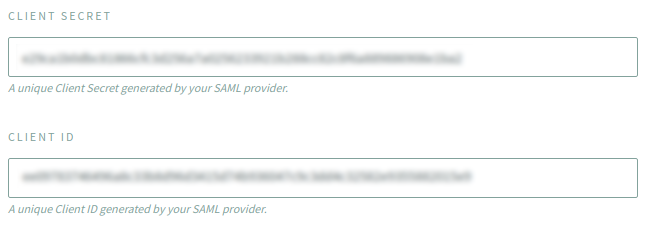
Force SAML Authentication
In your Organization’s SAML settings you can force SAML authentication, which means only users with the ability to use your organization’s Okta, PingID or OneLogin credentials can log in. If you previously invited non-SAML members (like third-party contractors) to your organization’s Team those members will receive an email but will lose access to the organization. This feature is designed to easily secure and restrict access to your org’s NodeSource organization, accounts.nodesource.com and NSolid Console.
You an activate the feature by activating the ‘Require SAML Authentication’ toggle in accounts.nodesource.com > Settings > SAML